Are you looking for an answer to the topic “How is Macaw differ from maca?“? We answer all your questions at the website Chiangmaiplaces.net in category: +100 Marketing Blog Post Topics & Ideas. You will find the answer right below.
The fairness of MACAW is much better than MACA. It handle hidden and exposed node problem better than MACA. ACK signal is send to the MAC layer, after every data frame. It also incorporate carrier detecting to additionally diminish collision.WLAN data transmission collisions can still happen, and MACA for Wireless (MACAW) is brought to extend the functionality of MACA. It demands nodes to send acknowledgments after every successful frame transmission. MACAW is commonly used in ad hoc networks.Multiple Access with Collision Avoidance for Wireless (MACAW) is a slotted medium access control (MAC) protocol widely used in ad hoc networks. Furthermore, it is the foundation of many other MAC protocols used in wireless sensor networks (WSN). The IEEE 802.11 RTS/CTS mechanism is adopted from this protocol.

Table of Contents
How does macaw extend Maca?
WLAN data transmission collisions can still happen, and MACA for Wireless (MACAW) is brought to extend the functionality of MACA. It demands nodes to send acknowledgments after every successful frame transmission. MACAW is commonly used in ad hoc networks.
What is Macaw in networking?
Multiple Access with Collision Avoidance for Wireless (MACAW) is a slotted medium access control (MAC) protocol widely used in ad hoc networks. Furthermore, it is the foundation of many other MAC protocols used in wireless sensor networks (WSN). The IEEE 802.11 RTS/CTS mechanism is adopted from this protocol.
ASN L8: MACA Problem and MACAW Protocol(Contention Based Protocol)
Images related to the topicASN L8: MACA Problem and MACAW Protocol(Contention Based Protocol)

How does Maca protocol work?
The MACA protocol works with the condition that the stations are synchronized and frame sizes and data speed are the same. It involves transmission of two frames called RTS and CTS prior to data transmission. RTS stands for Request to Send and CTS stands for Clear to Send.
On what basis macaw protocol is designed?
The design of MACAW is based on four observations: Relevant contention occurs at the receiver; sensing carrier at the sender (as in CSMA) is inappropriate. Congestion is location dependent. For fair allocation, collision (congestion) information must be shared among devices.
What is the difference between multiple access collision detection Maca and macaw for wireless )?
Advantages over MACA :
The fairness of MACAW is much better than MACA. It handle hidden and exposed node problem better than MACA. ACK signal is send to the MAC layer, after every data frame. It also incorporate carrier detecting to additionally diminish collision.
What are the two types of MAC protocols?
The classification of MAC protocols or types of MAC protocol or types of MAC are: Contention based protocols without reservation. Contention based protocols with reservation.
Which protocol is more bandwidth efficient Rtmac or maca PR explain?
Which protocol is more bandwidth efficient RTMAC or MACA/PR? RTMAC uses bandwidth efficiently than MACA/PR. MACA/PR has the possibility of having fragmented free slots not being used at all which reduces bandwidth efficiency whereas in RTMAC, the free slots may occur in between the reservation slots.
See some more details on the topic How is Macaw differ from maca? here:
What is difference between Maca and MACAW protocol?
Multiple Access with Collision Avoidance for Wireless (MACAW) is a slotted medium access control (MAC) protocol widely used in ad hoc networks.
Difference between CSMA and MACA – RF Wireless World
➨MACA is based on CSMA/CA. It adds “duration field” in RTS/CTS which intimates other terminals about their backoff time. ➨MACAW has been developed as …
What is Multiple Access With Colision Avoidance (MACA)?
WLAN data transmission collisions can still happen, and MACA for Wireless (MACAW) is brought to extend the functionality of MACA.
What is Macaw protocol? – Lynniezulu.com
In MACA, a wireless network node announces that it is going to send the data frame, …
What is Fama protocol?
These protocols are based on a new channel access discipline called floor acquisition multiple access (FAMA), which consists of both carrier sensing and a collision-avoidance dialogue between a source and the intended receiver of a packet.
What is hidden and exposed terminal?
The hidden terminal problem occurs when a terminal is visible from a wireless access point (APs), but not from other nodes communicating with AP. This situation leads the difficulties in medium access control sub-layer over wireless networking.
What is the advantage of Maca protocol?
Multiple Access with Collision Avoidance (MACA) is a slotted media access control protocol used in wireless LAN data transmission to avoid collisions caused by the hidden station problem and to simplify exposed station problem.
Does Maca solve exposed terminal problem?
Multiple Access with Collision Avoidance (MACA) is a medium access control (MAC) layer protocol used in wireless ad hoc network. It is used to solve the hidden terminal problem and exposed terminal problem.
How packets are transmitted in Maca?
In MACA-BI the receiver node initiates data transmission by transmitting a ready to receive (RTR) control packet to the sender. If it is ready to transmit, the sender node responds by sending a data packet. Thus data transmission in MACA-BI occurs through a two way handshake mechanism [1-3].
MACA and MACAW
Images related to the topicMACA and MACAW
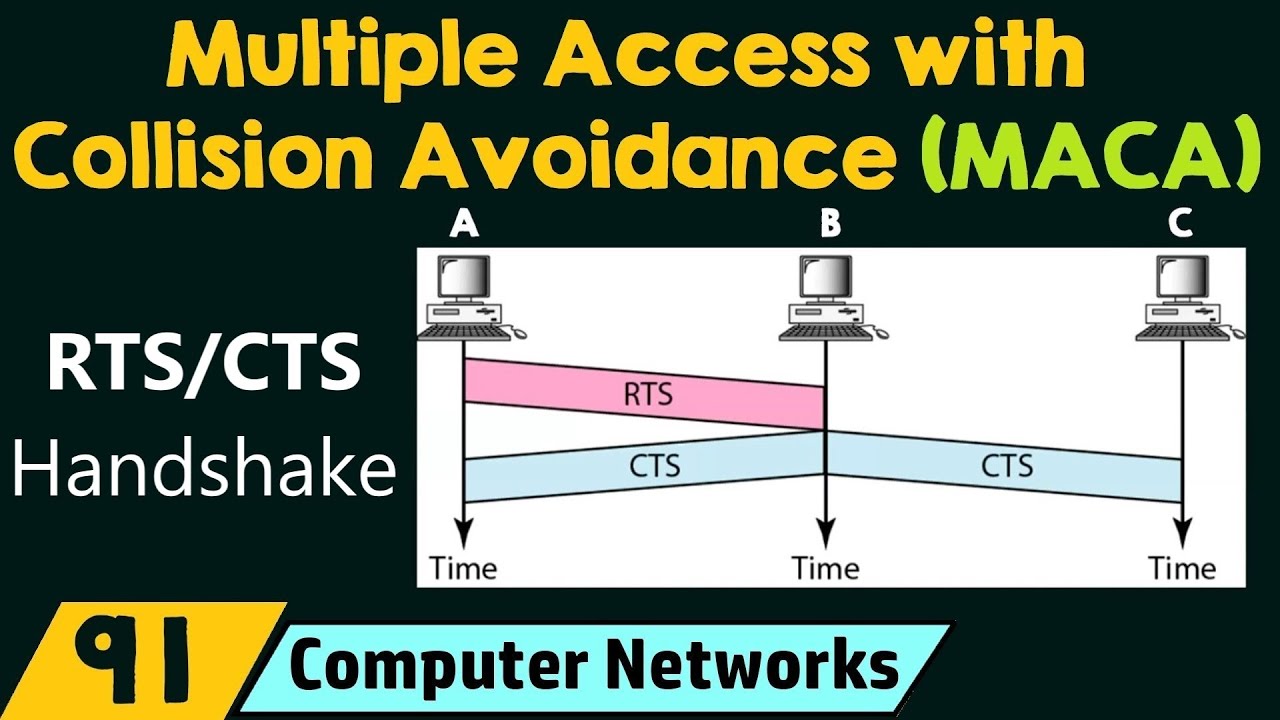
How does RTS CTS work?
The RTS/CTS Mechanism
When a node wants to transmit data to another node, it sends out a RTS ‘Request to Send’ packet. The receiver node replies with a packet called CTS ‘Cleared to Send’ packet. After the transmitter node receives the CTS packet, it transmits the data packets.
What is meant by the term ad hoc network?
Definition(s):
A wireless network that allows easy connection establishment between wireless client devices in the same physical area without the use of an infrastructure device, such as an access point or a base station.
Which protocol is used to avoid collisions on a wireless network?
Carrier sense multiple access/collision avoidance (CSMA/CA) is a protocol for carrier transmission in 802.11 networks. It was developed to minimize the potential of a collision occurring when two or more stations send their signals over a data link layer.
What is Aloha protocol?
ALOHA is a multiple access protocol for transmission of data via a shared network channel. It operates in the medium access control sublayer (MAC sublayer) of the open systems interconnection (OSI) model.
What is CSMA CD & CSMA CA?
CSMA/CD and CSMA/CA are the media access methods that govern how a device can transmit data to the network. CSMA/CD stands for Carrier Sense Multiple Access / Collision Detection. CSMA/CA stands for Carrier Sense Multiple Access/Collision Avoidance. Both methods are used in a single collision domain.
What is medium access control in mobile computing?
The medium access control (MAC) is a sublayer of the data link layer of the open system interconnections (OSI) reference model for data transmission. It is responsible for flow control and multiplexing for transmission medium. It controls the transmission of data packets via remotely shared channels.
Why Aloha is used in wireless medium?
(a) ALOHA – It was designed for wireless LAN but is also applicable for shared medium. In this, multiple stations can transmit data at the same time and can hence lead to collision and data being garbled. Pure Aloha: When a station sends data it waits for an acknowledgement.
What are the different features of MAC protocols?
- IEEE 802.11. This MAC protocol is a CSMA/CA-based protocol and implements control packets to avoid a collision as soon as possible. …
- Sensor S-MAC. This MAC protocol is CSMA/CA-based protocol and a well-known protocol in WSN [8. …
- Timeout T-MAC. …
- DSMAC. …
- WiseMAC. …
- TRAMA. …
- DMAC.
What is the full form of MAC address?
In a local area network (LAN) or other network, the MAC (Media Access Control) address is your computer’s unique hardware number. (On an Ethernet LAN, it’s the same as your Ethernet address.)
Which of the following is the main components of maca PR?
5.4.
There are three main components of this protocol: – A MAC protocol; – A reservation protocol; – A QoS routing protocol. MACA/PR differentiates between real-time packets and best-effort packets; it provides bandwidth to real-time traffic.
Multiple Access with Collision Avoidance (MACA)
Images related to the topicMultiple Access with Collision Avoidance (MACA)
Which routing protocol is used for small network?
RIP is not very scalable so is primarily used for small networks. RIP uses UDP to broadcast messages; port 520 is used by servers, whereas clients use a port above 1023. Another routing protocol is Open Short Path First (OSPF), which was developed after RIP.
What are different mobility models?
Mobility models are basically classified as stochastic, detailed, Hybrid and Trace based Realistic models. The stochastic models are based on random movements and the nodes are free to move in any direction. Example include Random waypoint model, Random walk and Random direction model.
Related searches to How is Macaw differ from maca?
- difference in black maca and maca
- macaw protocol tutorialspoint
- macaw protocol ppt
- how is macaw differ from maca
- macaw protocol is used in
- difference between maca and macaw protocol
- difference between black maca and regular maca
- in macaw data sending ds frame is of size
- what are the drawbacks of maca protocol
- what is false about maca protocol
- difference between maca and red maca
- macaw is used in
- macaw vs maca
- explain the importance of exposed terminal for designing mac protocol
Information related to the topic How is Macaw differ from maca?
Here are the search results of the thread How is Macaw differ from maca? from Bing. You can read more if you want.
You have just come across an article on the topic How is Macaw differ from maca?. If you found this article useful, please share it. Thank you very much.